If you manage a single cloud tenant with a single subscription, roles and responsibilities for security can usually be maintained by a small SecOps team.
But if your organization has dozens or hundreds of departments, the need for a much more hierarchical structure can quickly become difficult for a single security team to maintain control over.
So what can happen is departments are handed over the role of the security administrator for their own resources and users.
And before you know it, SecOps has lost control of who’s making changes to what.
Fear not, this isn’t a terrible thing, but it’s important to put checks in place to ensure simple practices are being followed.
One approach:
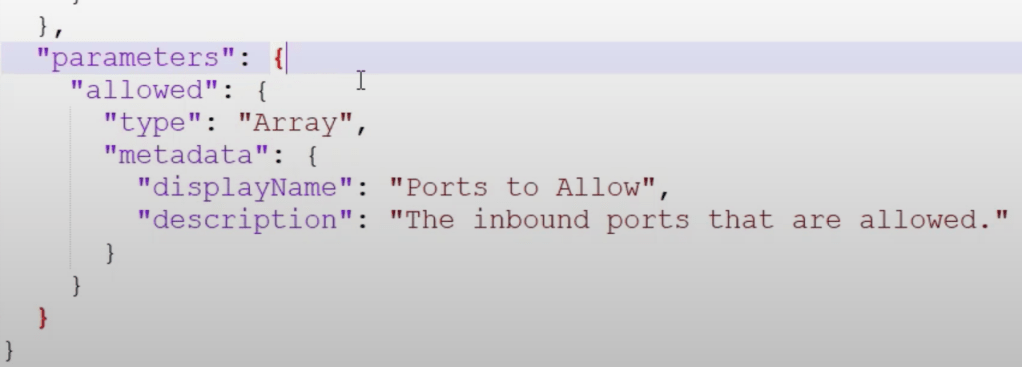
- Perform a security audit that provides a list of the security categories of interest. (This audit should provide both high level and lower level topics, so you can easily end up with hundreds of checks). Example high level topics:
- Identity & Access Controls
- Logging, Monitoring and Reporting
- Data Protection
- Network Security
- Endpoint Protection
- Inventory Management
- Configuration Management
- Vulnerability Management
- Create a list of relevant security checks from the above audit (this checklist is much shorter than the original security audit, since these departmental security admins have a much smaller list of security responsibilities).
- Identify a security owner for each relevant department/group
- Require each security owner to perform periodic checks and report back to the SecOps team.
Not only does the above approach provide clear security checks/responsibilities to the security owners, but it gives the SecOps team a way to track security in a growing organization without getting overwhelmed. It also ensures that as security owners come and go from the organization, that the new owners will be quickly identified by the SecOps team, thus avoiding gaps in maintaining security controls.