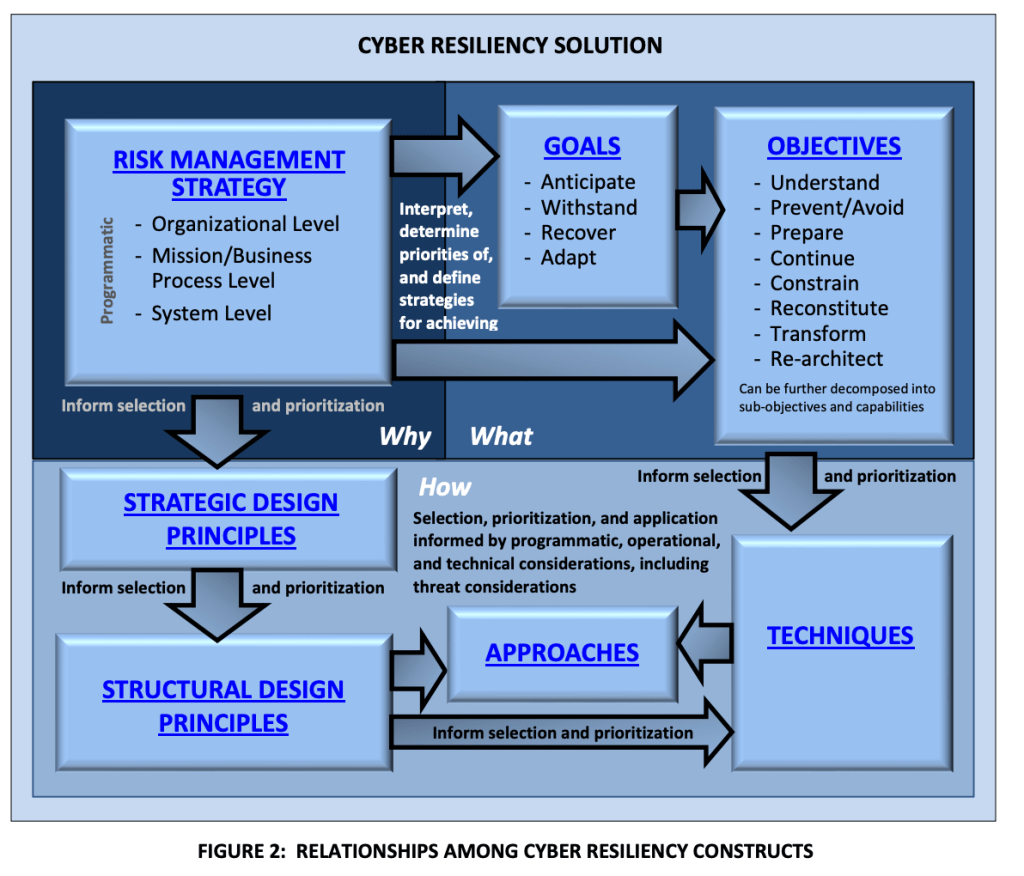
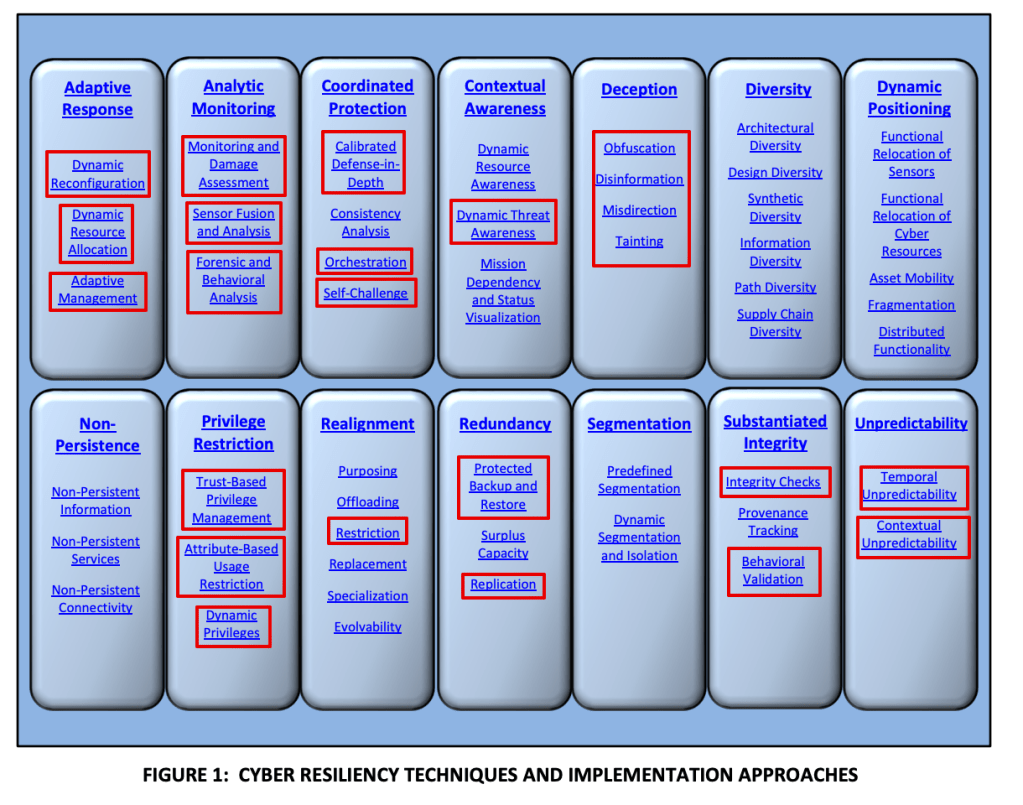
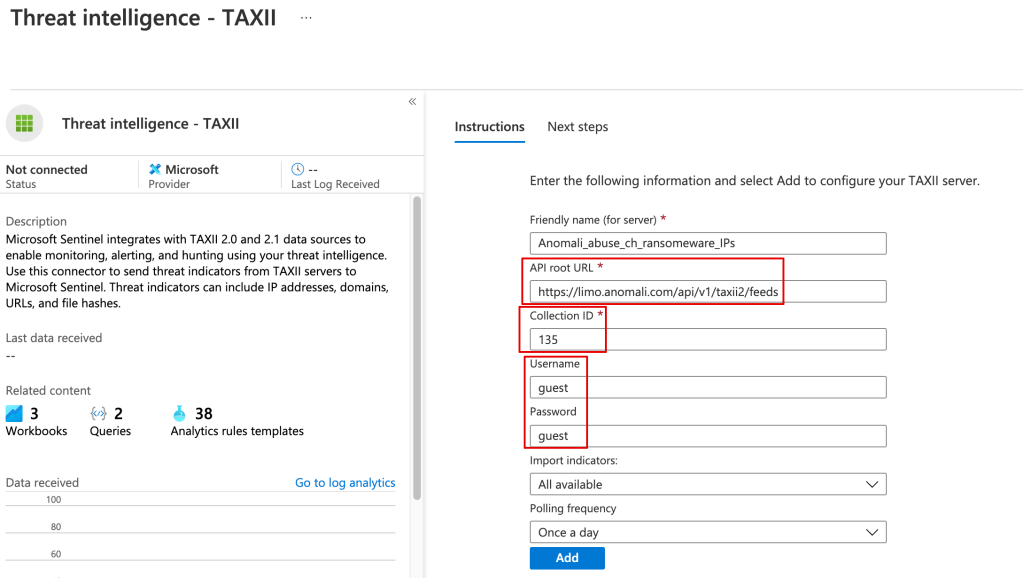
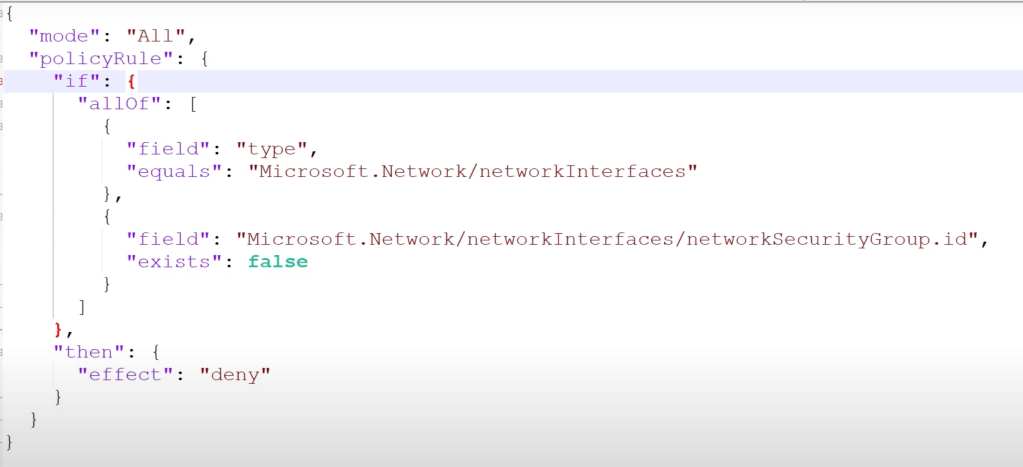
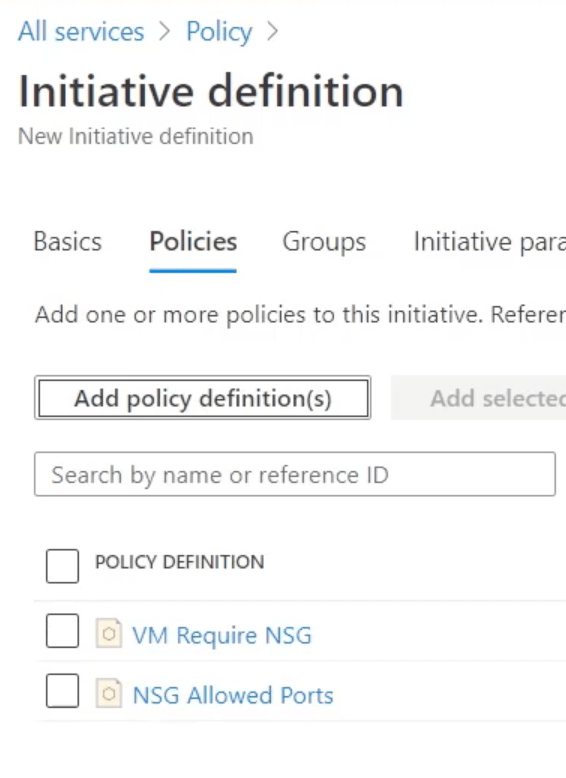
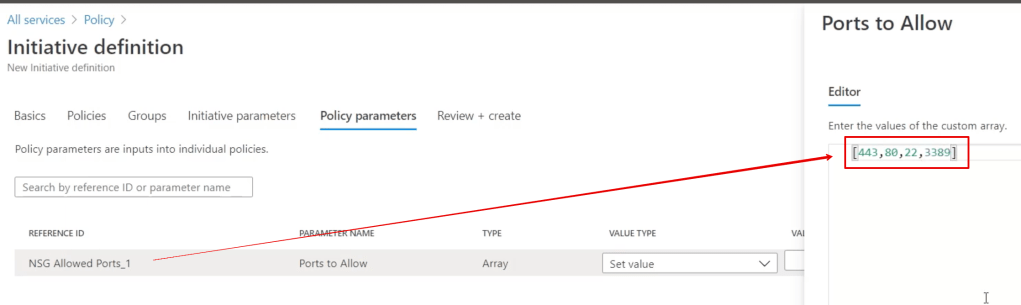
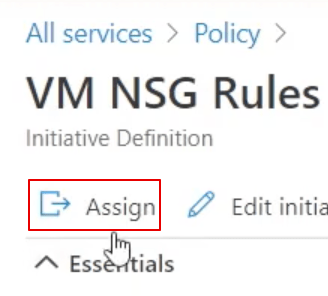
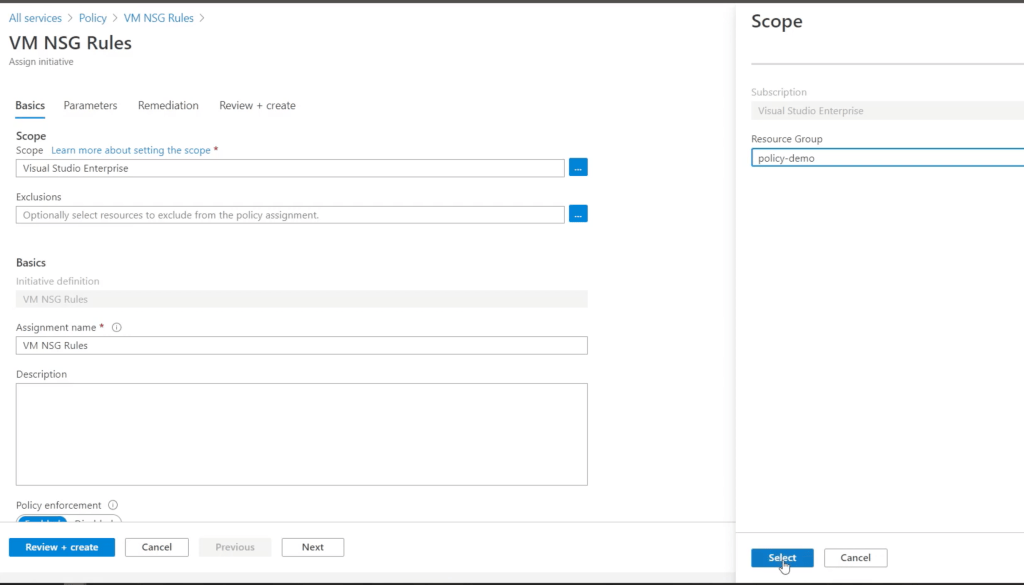
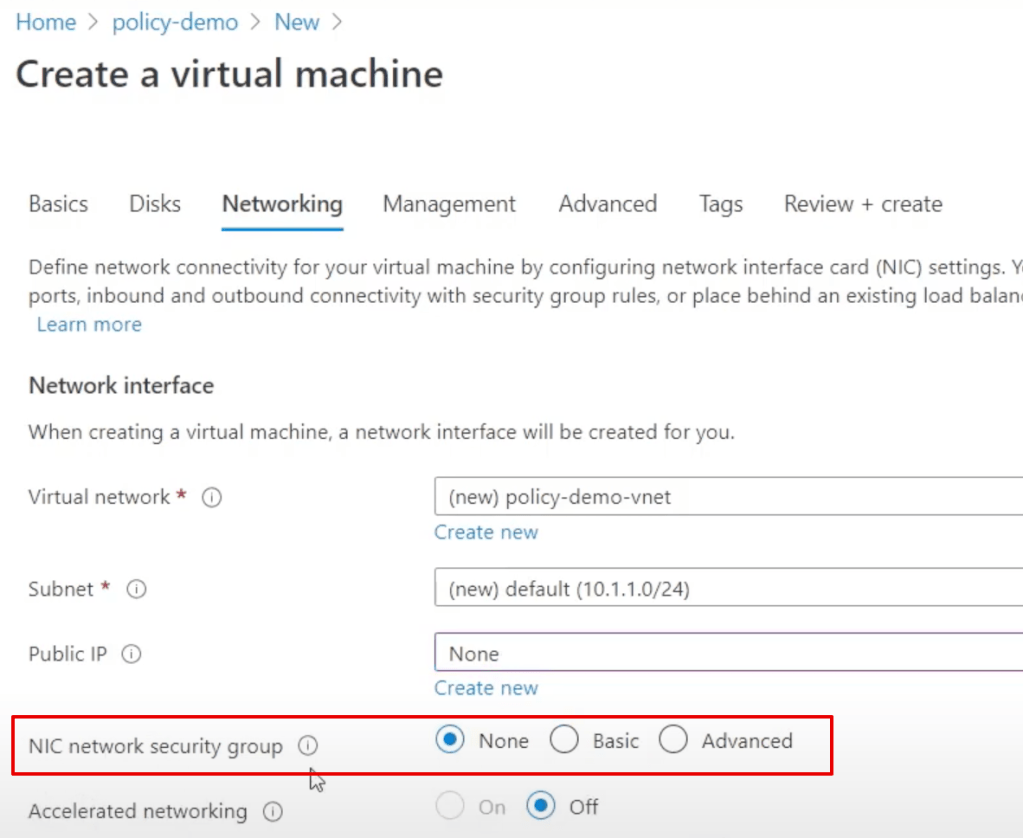
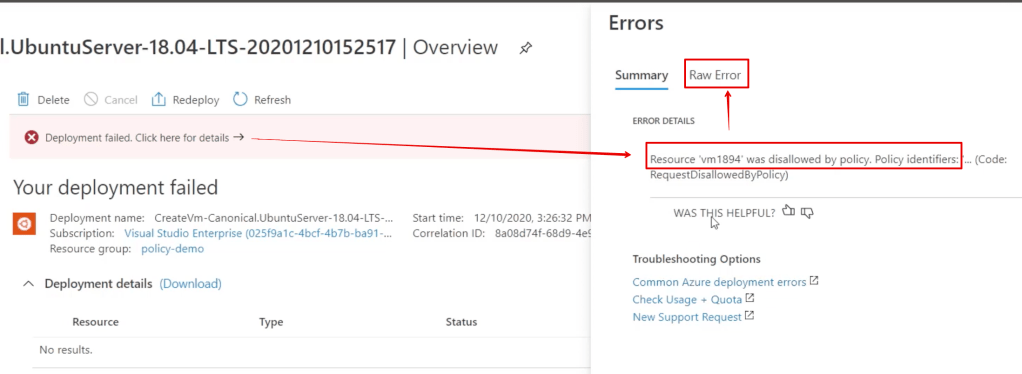
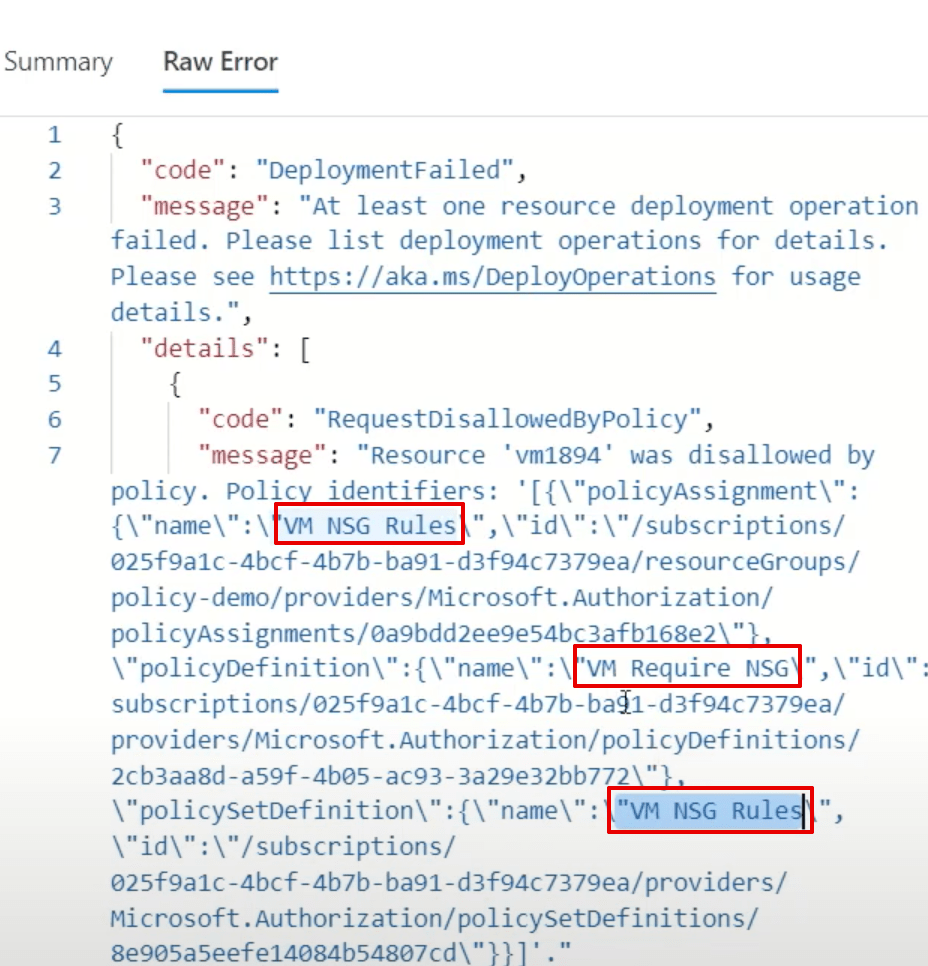
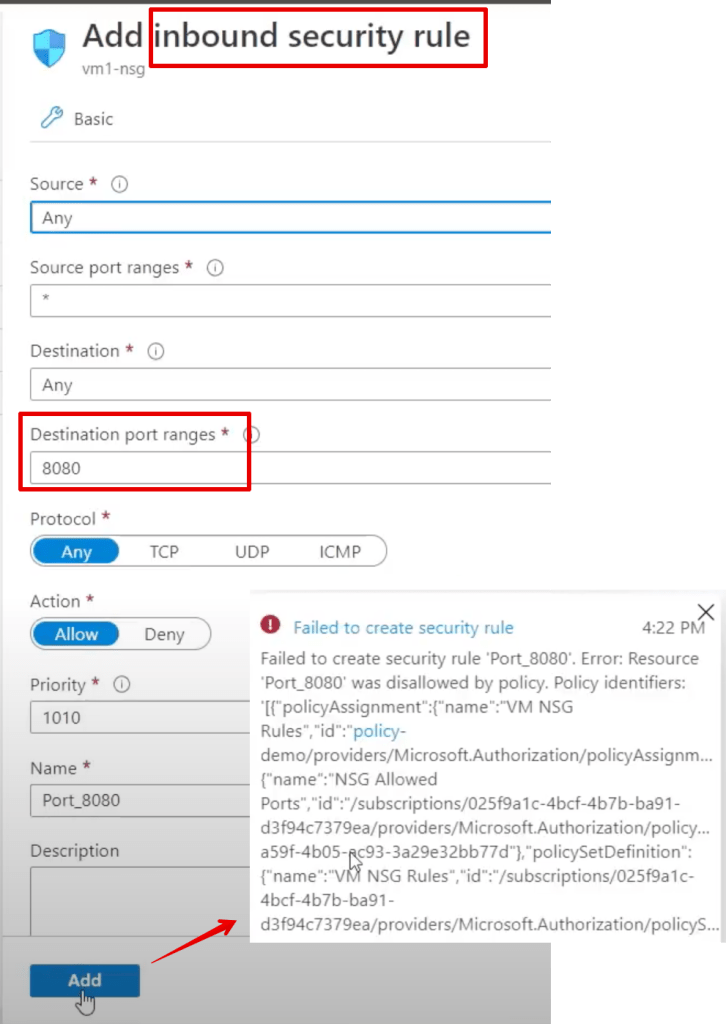
If you’re frequently involved with Microsoft security, it may be useful to maintain a list of the most common links.
If you’re a SOC analyst, some of these links will make good dashboards for your wall of 4k monitors.
If you’re a security engineer, this can be one of your checklists for walking around all things security related in the Microsoft cloud.
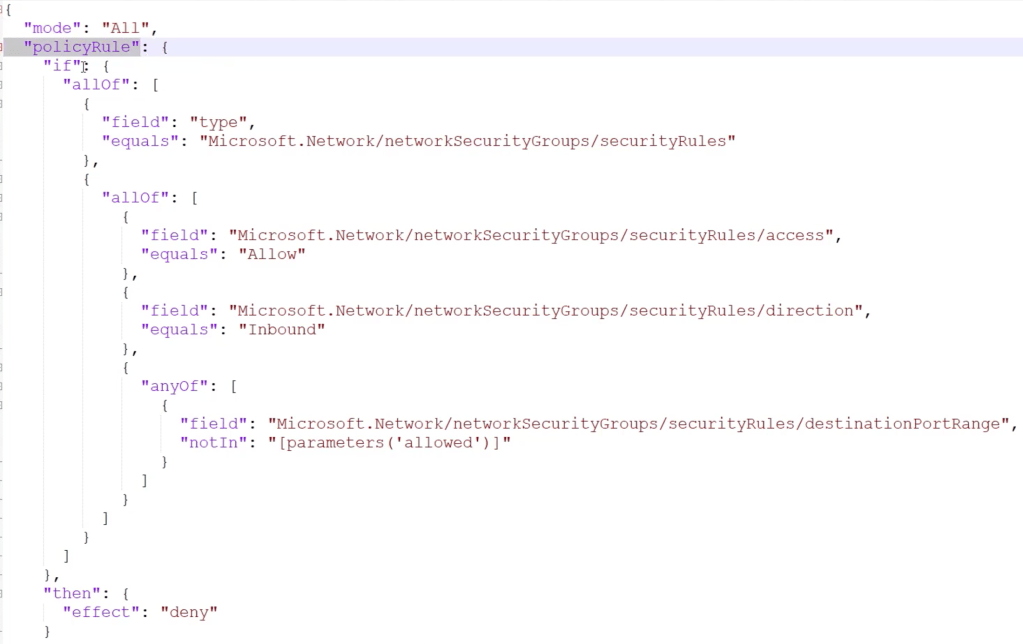
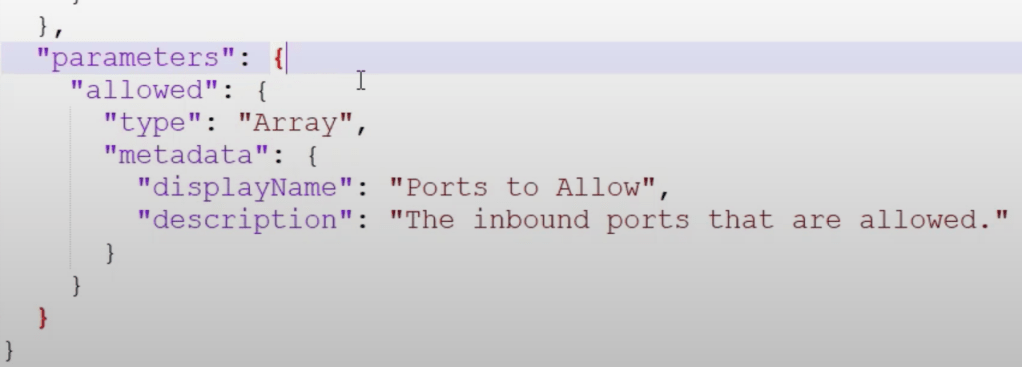
Since I don’t have any spreadsheet formatting plugins, the web links in the screenshot are listed below.
(This isn’t a comprehensive list of security related links, but something to grow on)
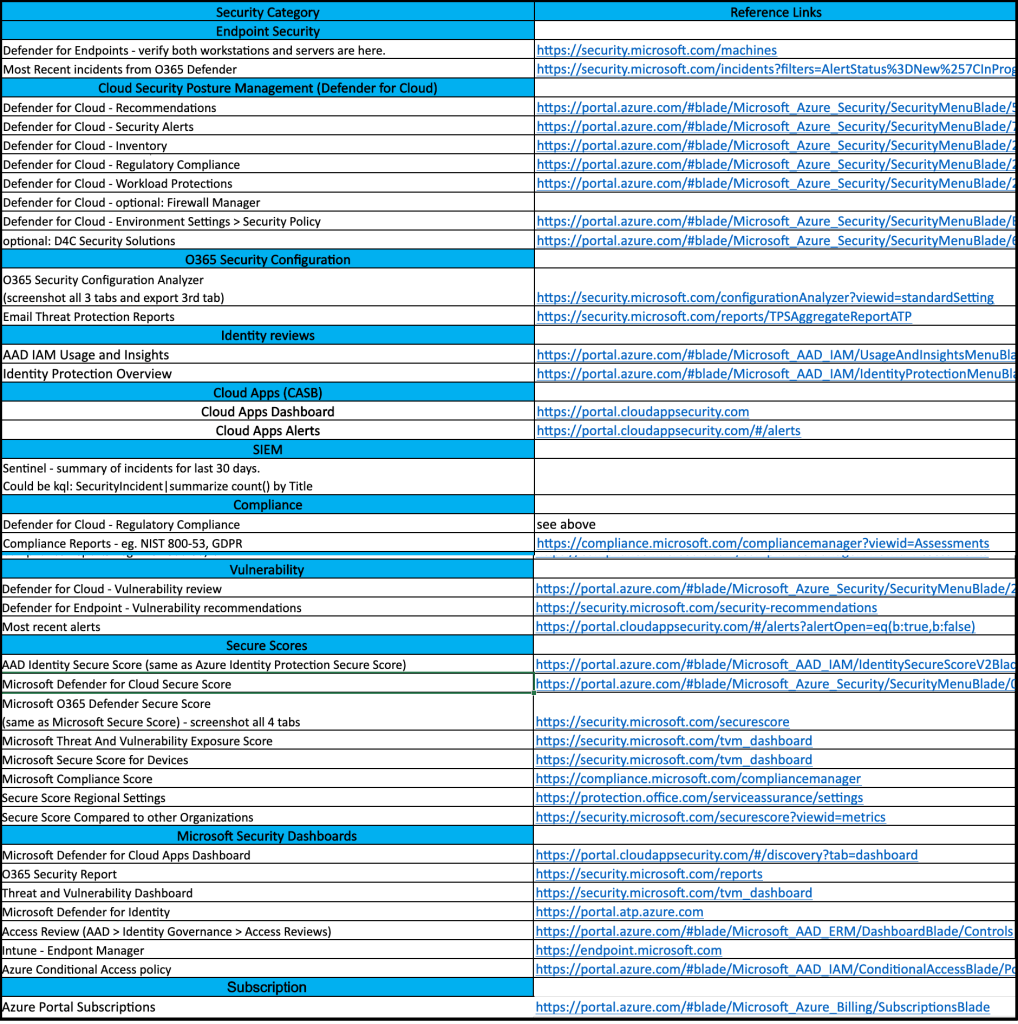
Reference Links
https://security.microsoft.com/machines https://security.microsoft.com/incidents?filters=AlertStatus%3DNew%257CInProgress https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/5 https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/7 https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/25 https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/22 https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/26 https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/EnvironmentSettings https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/6 https://security.microsoft.com/configurationAnalyzer?viewid=standardSetting https://security.microsoft.com/reports/TPSAggregateReportATP https://portal.azure.com/#blade/Microsoft_AAD_IAM/UsageAndInsightsMenuBlade/Azure%20AD%20application%20activity https://portal.azure.com/#blade/Microsoft_AAD_IAM/IdentityProtectionMenuBlade/Overview https://portal.cloudappsecurity.com https://portal.cloudappsecurity.com/#/alerts https://compliance.microsoft.com/compliancemanager?viewid=Assessments https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/26 https://security.microsoft.com/security-recommendations https://portal.cloudappsecurity.com/#/alerts?alertOpen=eq(b:true,b:false) https://portal.azure.com/#blade/Microsoft_AAD_IAM/IdentitySecureScoreV2Blade https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0 https://security.microsoft.com/securescore https://security.microsoft.com/tvm_dashboard https://compliance.microsoft.com/compliancemanager https://protection.office.com/serviceassurance/settings https://security.microsoft.com/securescore?viewid=metrics https://portal.cloudappsecurity.com/#/discovery?tab=dashboard https://security.microsoft.com/reports https://security.microsoft.com/tvm_dashboard https://portal.atp.azure.com https://portal.azure.com/#blade/Microsoft_AAD_ERM/DashboardBlade/Controls https://endpoint.microsoft.com https://portal.azure.com/#blade/Microsoft_AAD_IAM/ConditionalAccessBlade/Policies https://portal.azure.com/#blade/Microsoft_Azure_Billing/SubscriptionsBlade