Category: Zero Trust
OpenAI – What Should be Monitored?
Since the explosion of publicly accessible OpenAI, the question of how to monitor its use within an organization has been a frequently asked question.
Below are some topics relevant to the most common OpenAI services/features available today. Consider using these topics/suggestions as a starting point to creating a scope of topics relevant to security governance, and to help develop security policies for your organization.
Publicly Accessible OpenAI services
- Description: Web sites like OpenAI’s ChatGPT provide a wealth of knowledge and an opportunity to accelerate a user’s knowledge on an infinite number of topics.
- Security Policy Consideration: Pasting corporate information into a public facing site of any kind should be considered prohibitive.
Corporate Licensed OpenAI services
- Description: OpenAI resources such as Azure OpenAI can be enabled at low cost within the cloud. These AI models can be customized to solve complex challenges within an organization or provide public facing features which enhance a corporation’s service offerings.
- Security Policy Consideration: Creation of resources in openAI based tools such as Azure OpenAI Studio and PowerApps should be controlled and monitored by the security team.
End User OpenAI Related Productivity Tools
- Description: Microsoft’s Copilot is an example of end-user OpenAI tools that will change they way people work, and it will have a dramatic affect on their productivity.
- Security Policy Consideration: Authorized use of AI tools, such as Copilot should be monitored.
Be aware of ‘Self-Aware’ OpenAI Tools
Description: If you’ve used Auto-GPT, you might be concerned about the ability of OpenAI tools to be given full root/admin control to do whatever it takes to provide the answer to a question. This includes creation of scripts, adding/deletion of files, and even rebooting your pc.
Security Policy Consideration: Strict monitoring of any open source OpenAI tools that are running on enduser pc’s or on servers should be strictly monitored and approved for use.
Security Monitoring and Best Practices
- Monitoring of all use of AI generated activity should be monitored via EDR, CASB, SIEM etc.
- Discuss with your vendors the best practices on how their OpenAI tools can be monitored.
- Test/simulate the use of each OpenAI tool and validate your ability to monitor its activities, including individual user access and change controls.
US National Cybersecurity Strategy
Based on the recent publication of the US National Cybersecurity Strategy, here are some practical suggestions for implementing cybersecurity solutions that loosely map to its guidelines:
- Defend Critical Infrastructure by:
- Expanding the use of minimum cybersecurity requirements in critical sectors to ensure national security and public safety and harmonizing regulations to reduce the burden of compliance
Recommendation: Perform a gap analysis on your cybersecurity defenses. Start with a ‘master list of all recommended defenses and compare that to your organization’s tools’ Prioritize the implementation of any required defenses. Consider consolidation of security solutions under a single vendor’s licence agreement to save on costs. Create good architecture diagrams to describe your infrastructure from a cybersecurity perspective.
- Enabling public-private collaboration at the speed and scale necessary to defend critical infrastructure and essential services
Recommendation: Create an inventory of all critical assets. If you’re a small org then a manual inventory is fine, otherwise consider a mature asset collection tool to help with this (google ‘asset inventory cybersecurity’ and you’ll get plenty of hits). Use your asset inventory to categorize critical assets and use this information in your SIEM to help with better correlations.
- Defending and modernizing Federal networks and updating Federal incident response policy.
Recommendation: Review/create incident response policies and procedures. Consider creating specific response procedures that map to your SIEM incidents to improve clarity and incident response times.
- Disrupt and Dismantle Threat Actors by:
- Using all instruments of national power, making malicious cyber actors incapable of threatening the national security or public safety of the United States
- Strategically employing all tools of national power to disrupt adversaries
- Engaging the private sector in disruption activities through scalable mechanisms
- Addressing the ransomware threat through a comprehensive Federal approach and in lockstep with international partners.
Recommendation: Have a clear understanding of the ‘kill chains‘ that may affect your organization. Use Mitre ATT&CK and your favorite security sites to help research threat actor groups. Identify security tools needed to detect/block attackers. Test/validate the effectiveness of those tools using Red/Blue/Purple team events.
- Shape Market Forces to Drive Security and Resilience by:
- Placing responsibility on those within the digital ecosystem that are best positioned to reduce risk and shift the consequences of poor cybersecurity away from the most vulnerable in order to make the digital ecosystem more trustworthy
- Promoting privacy and the security of personal data
Recommendation: Move data to the cloud and implement a data protection solution that not only tags and categorizes your data but locks out access if it’s stolen.
- Shifting liability for software products and services to promote secure development practices
- Ensuring that Federal grant programs promote investments in new infrastructure that are secure and resilient.
- Invest in a Resilient Future by:
- Reducing systemic technical vulnerabilities in the foundation of the Internet and across the digital ecosystem while making it more resilient against transnational digital repression
Recommendation: Implement a robust vulnerability assessment solution. Note that moving all your assets to the cloud can make this far easier to manage and can greatly benefit the effectiveness of your CSPM and SIEM.
- Prioritizing cybersecurity R&D for next-generation technologies such as postquantum encryption, digital identity solutions, and clean energy infrastructure and developing a diverse and robust national cyber workforce.
- Forge International Partnerships to Pursue Shared Goals by:
- Leveraging international coalitions and partnerships among like-minded nations to counter threats to the digital ecosystem through joint preparedness, response, and cost imposition
- Increasing the capacity of partners to defend themselves against cyber threats, both in peacetime and in crisis; and working with allies and partners to make secure, reliable, and trustworthy global supply chains for information and communications technology and operational technology products and services.
Recommendation: Although many are reluctant to go back to the IBM days of putting all your security solutions into a single basket, cloud vendors and MSSPs have made great progress in the past 5+ years to provide a long list of services under one roof. When looking for one security product it’s very important to think broader and understand the interconnected values between all of your other security tools (XDR!). Security decision makers will often find that re-shuffling several of their security solutions makes more sense than just adding them one brick at a time.
Making Security Fun with Microsoft Cloud Games
This is a really fun way to learns some practical skills with Microsoft Cloud security tools.
I would recommend this for anyone who has a Microsoft E5 license or anyone using Microsoft cloud based products who is ready to get serious about securing their cloud and on-prem environment with Microsoft security tools.
This is not for beginners.
It’s expected you have at least a basic understanding of what these security tools are shown in this screenshot from the game:

Expect to spend at least a couple of hours playing the game.
Have fun!
Zero Trust – A simple Approach for Azure Enterprises
Zero Trust sounds very enticing, but feels overwhelming as much as any other standards based framework.
However there are some quick wins in the Azure world, and all you need is:
- A good checklist (The Microsoft Zero Trust Assessment Quiz)
- A Microsoft Sentinel workbook (see below)
In addition, Microsoft has a ton of direction around Zero Trust like:
If you prefer to save some reading time, I’ve taken Microsoft Zero Trust Assessment Quiz results and compressed it into a clean list of questions here:
Microsoft has also added a Zero Trust workbook to Azure Sentinel, so if you’re using their SIEM, there’s an excellent report that you can export and have a full list of security tool recommendations that you likely already own (depending if you have an E3 or E5 license)
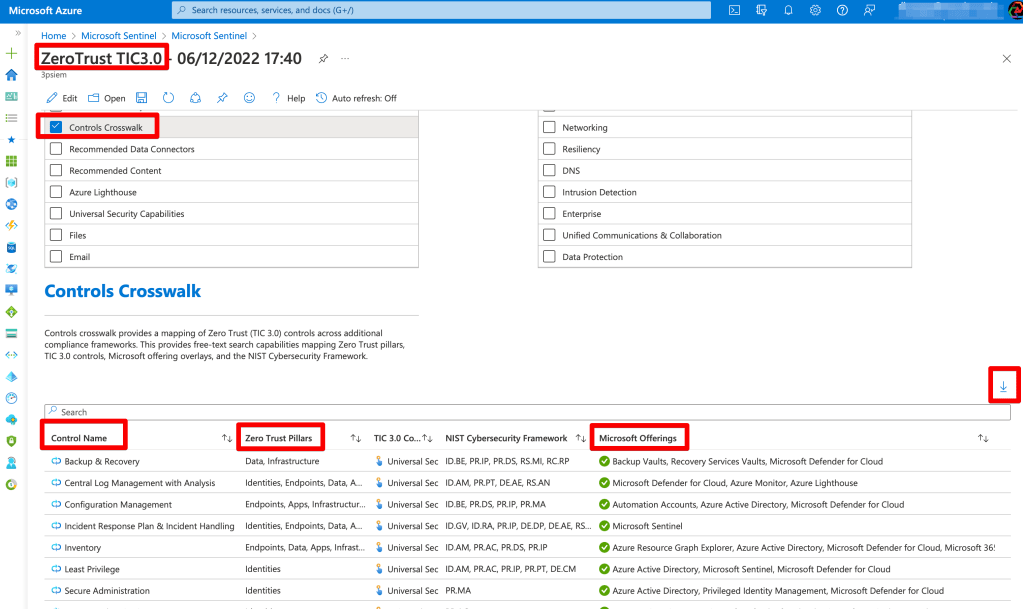
If you’re familiar with the resources under ‘Microsoft Offerings’ then you can begin planning your Zero Trust controls around these features. If you’re not familiar then now it the time to begin learning and proposing a Zero Trust approach around these tools.
Enjoy!
