Category: Security
Microsoft SC-100 Security Architect Expert Certification Study Reference
If you’re studying for the SC-100 or you just want a decent reference to many of Microsoft’s security topics please feel free to try my reference sheet attached below.
Note that almost all of the (233) web links in this sheet reference the Microsoft Learn site (https://learn.microsoft.com) so you don’t have to worry about them being malicious :).
Enjoy!
Creating Your Own Threat Actor Research Bot
There is nothing perfect about auto-gpt but like chatgpt it’s another tool that if used creatively can be used to achieve amazing things I wouldn’t have even considered doing 2 months ago.
If you want to read about my odd path of discovery in building this script, see the short story below, otherwise just enjoy the script.
Ramon Gomez on LinkedIn had the idea of using auto-gpt to find threat actor in the new as they relate to the United States Energy sector.
His attempts at using auto-gpt failed but I gave it a try anyways.
Sure enough it failed for me too, but I carefully read the output from auto-gpt and I could see what it was trying to do:
- download the enterprise-attack.json file from Mitre – this is a full ‘database’ of all things Mitre ATT&CK and it includes information about threat actors and some of the industries that they’re associated with.
- create an run a python script that reads enterprise-attack.json and extract the threat actors associated with the US energy sector. – this script had syntax errors so it was never going to run, but it tried…
- find a list of reliable new web sites that are related to cyber news. – this worked so I had a list of possible sites, but they weren’t perfect..
- create another python script that scraped the news sites for information associated with the threat actors – again it tried and failed.
Although auto-gpt tried and failed, it had an excellent approach to the problem.
And using ‘regular’ chatgpt I was able to ask the same sorts of questions and get much better answers.
Finally, as a result, chatgpt (and I) came up with the script you see below.
Note that this script has flaws, like some of the urls aren’t useful (but some are), but it does in fact work! enjoy.
import requests
from bs4 import BeautifulSoup
# Define a dictionary of threat actor names and their aliases
threat_actors = {
'APT1': ['Comment Crew'],
'Lazarus': ['Lazarus'],
'APT29': ['Cozy Bear'],
'APT32': ['OceanLotus Group']
}
# Define the URLs for the news resources
# Loop through the URLs and extract relevant web page URLs
# Define the URLs of the news resources
urls = [
'https://www.fireeye.com/blog/threat-research.html',
'https://www.kaspersky.com/blog/tag/apt',
'https://www.ncsc.gov.uk/news/reports',
'https://thehackernews.com/search/label/apt',
'https://www.recordedfuture.com/apt-group-threat-intelligence/',
'https://www.anomali.com/blog/threat-research'
]
webpage_urls = []
for url in urls:
html = requests.get(url).text
soup = BeautifulSoup(html, 'html.parser')
for link in soup.find_all('a'):
href = link.get('href')
for actor in threat_actors:
if actor in link.text or any(alias in link.text for alias in threat_actors[actor]):
webpage_urls.append(href)
# Print the extracted webpage URLs
for url in webpage_urls:
print(url)
Use ChatGPT to Search Mitre ATT&CK More Effectively
My python fu has never been above beginner, so writing scripts to use Mitre’s ATT&CK json files was always a hit and miss effort.
So I asked chatgpt to write it for me and after several back and forth tweaks and coding errors ‘we’ came up with these 2 which I find pretty useful.
To use the scripts, simply run “python <script>” and it will dump the results to a csv file (the first script requires you the first download the json file but the 2nd one doesn’t – see comments).
If you don’t like them exactly the way they are, paste them into chatgpt and simply ask it to make some modifications, eg:
- Add a header row
- Sort by the first column
- Only include these fields: technique_id,technique_name,tactic_name,platforms
- Use a comma as the field separator
- rather than reading from a local json file, read from the web version of enterprise-attack.json
ATT&CK_Tactic_Technique_LogSource.py
import json
# Load the MITRE ATT&CK Enterprise Matrix from the JSON file
# https://raw.githubusercontent.com/mitre/cti/master/enterprise-attack/enterprise-attack.json
with open('enterprise-attack.json', 'r') as f:
data = json.load(f)
# Open a file to write the output to
with open('output.csv', 'w') as f:
# Print the header row
f.write("technique_id,technique_name,tactic_name,platforms,permissions_required\n")
# Loop through each technique in the JSON file and print its fields
for technique in data['objects']:
# Extract the technique ID and name
if 'external_references' in technique and len(technique['external_references']) > 0:
technique_id = technique['external_references'][0].get('external_id', '')
else:
technique_id = ''
technique_name = technique.get('name', '')
# Extract the required platforms, if any
platforms = ",".join(technique.get('x_mitre_platforms', []))
# Extract the required permissions, if any
permissions_required = ",".join(technique.get('x_mitre_permissions_required', []))
# Extract the tactic name, if any
tactic_name = ""
if 'kill_chain_phases' in technique and len(technique['kill_chain_phases']) > 0:
tactic_name = technique['kill_chain_phases'][0].get('phase_name', '')
# Write the technique fields to the output file in CSV format
if technique_id and technique_name:
f.write(f"{technique_id},{technique_name},{tactic_name},{platforms},{permissions_required}\n")
# Read the contents of the output file into a list of lines
with open('output.csv', 'r') as f:
lines = f.readlines()
# Sort the lines based on the technique_id column
lines_sorted = sorted(lines[1:], key=lambda x: x.split(',')[0])
# Write the sorted lines back to the output file
with open('output.csv', 'w') as f:
f.write(lines[0])
f.writelines(lines_sorted)ATT&CK_All_Raw_Fields.py
import json
import urllib.request
# Load the JSON file from the URL
url = "https://raw.githubusercontent.com/mitre/cti/master/enterprise-attack/enterprise-attack.json"
response = urllib.request.urlopen(url)
data = json.loads(response.read())
# Create a list of all the field names
field_names = []
for technique in data["objects"]:
for field in technique:
if field not in field_names:
field_names.append(field)
# Add a header column to the field names
field_names_with_header = ["Header"] + field_names
# Write the data to a file with ";" as the delimiter
with open("enterprise-attack.txt", "w") as txt_file:
# Write the header row
header_row = ";".join(field_names_with_header) + "\n"
txt_file.write(header_row)
# Write the data rows
for i, technique in enumerate(data["objects"]):
values = [str(technique.get(field, "")).replace("\n", "") for field in field_names]
row = f";T{i+1}" + ";" + ";".join(values) + "\n"
txt_file.write(row)Microsoft Cloud Licensing and Cost Summary
Here’s a simple high level guide to navigating Microsoft licensing from a security perspective.
This guide won’t go into the details of ‘why’ you need these licenses, and it won’t discuss the operational costs of implementing these security solutions.
Your main reference for Microsoft enterprise licensing is here!
(don’t worry if you’re not in the US, it will ask you to switch)
On the left hand side of this page is a pdf you should download and really get to know:
Budgeting for security in any organization can be a challenge. Let’s assume you’re taking the leap with Microsoft but you want to work it into your budget.
Consider E5 licenses for a subset of users and E3 for the rest.
This will allow you to optimize the use of the security related features for your critical infrastructure and then grow out to the larger cost of protecting everything.
P1 vs P2
Next look at the P1 vs P2 features. If you have that E5 license then you’re mostly set with the P2 features since they’re included with E5.
If you have E3 then consider adding all of the P2 features until it makes more sense cost-wise to switch to E5. The order in which you add the P2 features will depend on your security priorities.
Don’t shrug off the importance of many of these P2 features. Here are some links to look at for more information:
Additional cost considerations:
- DDoS protection
- WAF
- SIEM – Microsoft Sentinel
- EASM – External Attack Surface Management
See the link for the Pricing Calculator below to dig into the cost of these additional services.
References:
M365 Licensing (includes everything related to E3, E5, P1, P2, etc.)
Defender for Cloud Pricing
Pricing Calculator – select the ‘Security’ side menu and go from there
US National Cybersecurity Strategy
Based on the recent publication of the US National Cybersecurity Strategy, here are some practical suggestions for implementing cybersecurity solutions that loosely map to its guidelines:
- Defend Critical Infrastructure by:
- Expanding the use of minimum cybersecurity requirements in critical sectors to ensure national security and public safety and harmonizing regulations to reduce the burden of compliance
Recommendation: Perform a gap analysis on your cybersecurity defenses. Start with a ‘master list of all recommended defenses and compare that to your organization’s tools’ Prioritize the implementation of any required defenses. Consider consolidation of security solutions under a single vendor’s licence agreement to save on costs. Create good architecture diagrams to describe your infrastructure from a cybersecurity perspective.
- Enabling public-private collaboration at the speed and scale necessary to defend critical infrastructure and essential services
Recommendation: Create an inventory of all critical assets. If you’re a small org then a manual inventory is fine, otherwise consider a mature asset collection tool to help with this (google ‘asset inventory cybersecurity’ and you’ll get plenty of hits). Use your asset inventory to categorize critical assets and use this information in your SIEM to help with better correlations.
- Defending and modernizing Federal networks and updating Federal incident response policy.
Recommendation: Review/create incident response policies and procedures. Consider creating specific response procedures that map to your SIEM incidents to improve clarity and incident response times.
- Disrupt and Dismantle Threat Actors by:
- Using all instruments of national power, making malicious cyber actors incapable of threatening the national security or public safety of the United States
- Strategically employing all tools of national power to disrupt adversaries
- Engaging the private sector in disruption activities through scalable mechanisms
- Addressing the ransomware threat through a comprehensive Federal approach and in lockstep with international partners.
Recommendation: Have a clear understanding of the ‘kill chains‘ that may affect your organization. Use Mitre ATT&CK and your favorite security sites to help research threat actor groups. Identify security tools needed to detect/block attackers. Test/validate the effectiveness of those tools using Red/Blue/Purple team events.
- Shape Market Forces to Drive Security and Resilience by:
- Placing responsibility on those within the digital ecosystem that are best positioned to reduce risk and shift the consequences of poor cybersecurity away from the most vulnerable in order to make the digital ecosystem more trustworthy
- Promoting privacy and the security of personal data
Recommendation: Move data to the cloud and implement a data protection solution that not only tags and categorizes your data but locks out access if it’s stolen.
- Shifting liability for software products and services to promote secure development practices
- Ensuring that Federal grant programs promote investments in new infrastructure that are secure and resilient.
- Invest in a Resilient Future by:
- Reducing systemic technical vulnerabilities in the foundation of the Internet and across the digital ecosystem while making it more resilient against transnational digital repression
Recommendation: Implement a robust vulnerability assessment solution. Note that moving all your assets to the cloud can make this far easier to manage and can greatly benefit the effectiveness of your CSPM and SIEM.
- Prioritizing cybersecurity R&D for next-generation technologies such as postquantum encryption, digital identity solutions, and clean energy infrastructure and developing a diverse and robust national cyber workforce.
- Forge International Partnerships to Pursue Shared Goals by:
- Leveraging international coalitions and partnerships among like-minded nations to counter threats to the digital ecosystem through joint preparedness, response, and cost imposition
- Increasing the capacity of partners to defend themselves against cyber threats, both in peacetime and in crisis; and working with allies and partners to make secure, reliable, and trustworthy global supply chains for information and communications technology and operational technology products and services.
Recommendation: Although many are reluctant to go back to the IBM days of putting all your security solutions into a single basket, cloud vendors and MSSPs have made great progress in the past 5+ years to provide a long list of services under one roof. When looking for one security product it’s very important to think broader and understand the interconnected values between all of your other security tools (XDR!). Security decision makers will often find that re-shuffling several of their security solutions makes more sense than just adding them one brick at a time.
Do you really need an NIDS anymore?
I had a client the other day asking for my recommendations on a NIDS platform.
Back in the day, NIDS was the ONLY security tool many corporations depends on to detect malicious activity. Many of the top MSSPs would build service contracts just around firewall and NIDS.
It’s worth questioning the value of NIDS in today’s day as EDR and XDR gets better and better.
And if you think of XDR as also including ‘smart’ firewalls like Palo Alto, and with proper network segmentation, you have to consider if NIDS is a worthy expenditure.
And if your DMZ has moved to or integrated with the cloud there are different ways to monitor/protect your sensitive assets than NIDS.
Just a few things to consider when trying to balance security value with your budget.
More references on this topic (Thanks Kevin!!!)
https://www.pratum.com/blog/262-why-intrusion-detection-and-prevention-systems-are-still-important
SIEM Use Case Guide – Part 3
Real World Examples
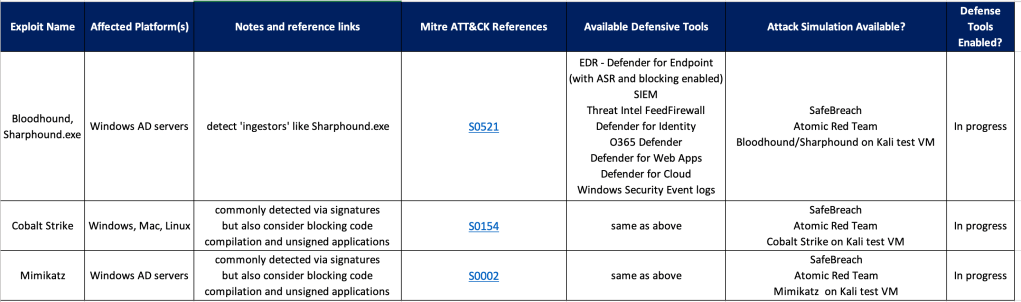
In this section let’s take the real world example of Bloodhound and discuss defensive measures for that use case.
Bloodhound
Step 1: Know thy Enemy.
Have a good list of threat intelligence sites (eg Mitre) that you can use to learn about an attack group or a specific exploit. Bloodhound uses ‘ingestors’ like Sharphound to collect information which it then uses to map out an attack path. So when looking for defenses you may need to look at the ingestors, not Bloodhound itself (although Sharphound may run as a sub-command within Bloodhound).
Step 2: Plan your defenses and build a Blue Team toolkit.
There are many ways to detect and block an exploit, depending on the conditions. But don’t take too much time thinking about the best way to do it when there are some easy wins that you can do right away, for example:
- Ensure an EDR (and AntiMalware) is installed on all endpoints, and run reports to ensure their rules/signatures are all kept updated.
- If the EDR vendor provides advanced features, make sure they’re enabled for optimal defenses – eg. enable blocking mode, enable advanced configurations such as Microsoft Defender ASR (Attack Surface Reduction)
- Configuration Policies – Use tools like Microsoft Endpoint Manager (with Intune) to configure policies on your endpoints to provide a base ‘hardening’ for your devices. Ensure logging is enabled on all servers, including advanced logging for Powershell. If you’re using 1 or more cloud platforms you should be managing your infrastructure’s security policies with a CSPM (cloud security posture management) like Microsoft Defender for Cloud – this can also add additional defenses like FIM – File Integrity Management.
Step 3: Build Process For Faster Response
Once you have a list of tools/methods for building defenses, create a checklist and start filling it out. You’ll find that after adding a few rows a common pattern will arise for similar exploits, so your ‘Defender’ job should get a bit easier over time.
Example Defender Framework/Checklist
See also:
Microsoft Ignite 2022 – START HERE
https://news.microsoft.com/ignite-2022-book-of-news/
https://ignite.microsoft.com/en-US/home
The list of Ignite presentation topics is HUGE!!!
Fortunately, Microsoft provides MVPs with an quick reference sheet so we can share our top picks with you.
So here are my top picks for security topics from Microsoft Ignite (and a few other non-security topics):
Rob Lefferts, CVP of PM, Modern Protection and SOC
https://ignite.microsoft.com/en-US/speakers/66804f79-fa68-4762-8f82-45798387e70e?source=/speakers
Shawn Bice, CVP, Cloud Security
https://ignite.microsoft.com/en-US/speakers/0e6b8553-7111-4422-94e0-04a8dddbd678?source=/speakers
What’s new in SIEM and XDR: Attack disruption and SOC empowerment
https://ignite.microsoft.com/en-US/sessions/e1f4b983-55d3-4048-8e90-9c22c4362e6b
Zero Trust as Business Driver: 3 Discrete Scenarios
https://ignite.microsoft.com/en-US/sessions/9974d5a2-b241-4ede-ab2d-c2cd1b7a83be
From Code to Cloud: A new Approach to Integrating Multicloud Security
https://ignite.microsoft.com/en-US/sessions/28f61a40-f1e6-43d8-9fd0-e3c8c6267bac
Secure access and improve efficiency with Microsoft Entra
https://ignite.microsoft.com/en-US/sessions/538bf946-a7bf-46dc-809f-9fbda241f918
Protect Everything, Everywhere With Comprehensive Security
https://ignite.microsoft.com/en-US/sessions/17bbd01d-4e26-4e2e-9eec-3a060b477eda?source=sessions
Azure Arc
https://ignite.microsoft.com/en-US/sessions/50f1092f-6209-4349-b02e-9ad2872ad136?source=sessions
https://azure.microsoft.com/en-us/products/azure-arc/hybrid-data-services/#overview
Azure Monitor
https://techcommunity.microsoft.com/t5/azure-observability-blog/bg-p/AzureObservabilityBlog
Azure – Postman integrations
Supply Chain Management Certification
Microsoft Cloud for Sustainability
Power Automate
Top 5 Cybersecurity Capabilities
5 cybersecurity capabilities announced at Microsoft Ignite 2022
Microsoft Entra
https://ignite.microsoft.com/en-US/sessions/538bf946-a7bf-46dc-809f-9fbda241f918?source=sessions
https://www.microsoft.com/en-us/security/business/microsoft-entra
Microsoft Sentinel
Microsoft Purview
Making Security Fun with Microsoft Cloud Games
This is a really fun way to learns some practical skills with Microsoft Cloud security tools.
I would recommend this for anyone who has a Microsoft E5 license or anyone using Microsoft cloud based products who is ready to get serious about securing their cloud and on-prem environment with Microsoft security tools.
This is not for beginners.
It’s expected you have at least a basic understanding of what these security tools are shown in this screenshot from the game:

Expect to spend at least a couple of hours playing the game.
Have fun!
