Mitre ATT&CK provides so many ways to quantitatively think about approaches for defending against attackers.
However it can be challenging to map the ATT&CK matrix to to real-world defense methods.
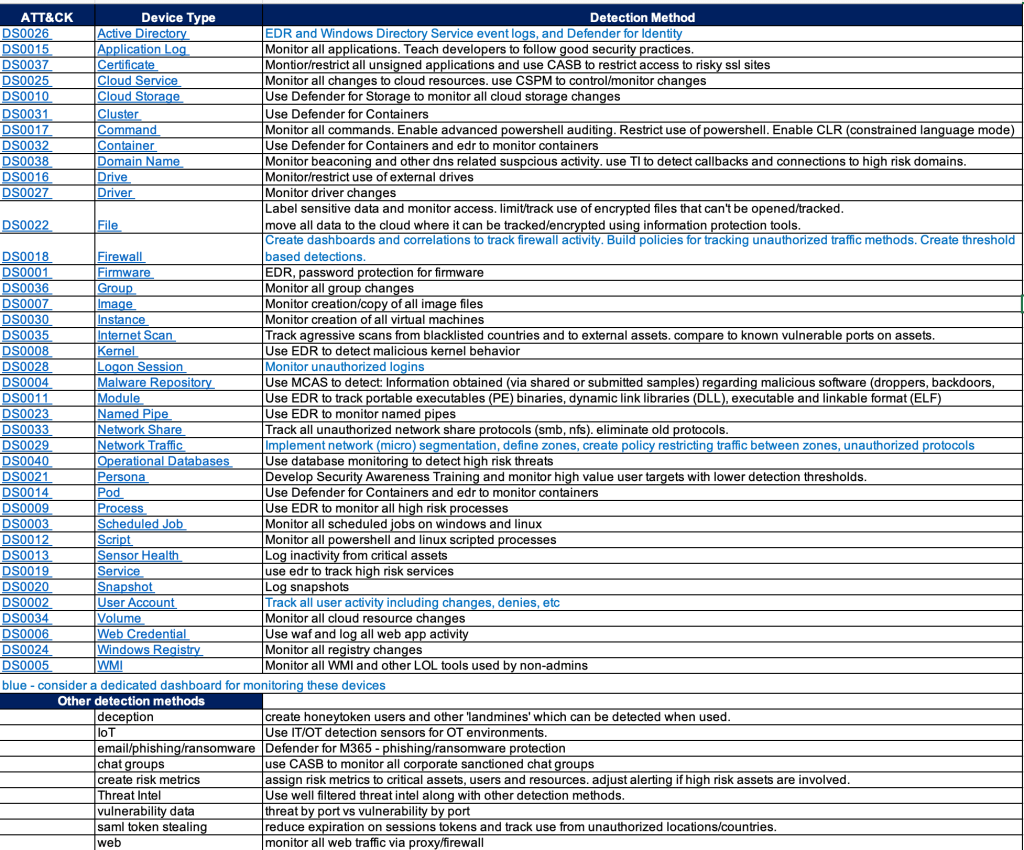
One approach is to look at the ATT&CK data sources and research detections that would map to those data sources.
This still requires some experience and a bit of guessing since there doesn’t appear to be an easy button way to map data sources to detection tools.
Endpoint Detection vendors have done a pretty good job mapping detections to ATT&CK techniques but few of them share their mappings in a simple spreadsheet – that would greatly help validate your detection gaps.
SIEM products like Microsoft Sentinel have done a good job mapping detection rules AND log sources to ATT&CK.
The chart below is an example of an easy way to provide a path forward on where to focus efforts for detections. It also provides a gap analysis for any obvious security tools that may be missing in your environment.
And hopefully my short detection method recommendations will give you some ideas or at least stir conversation.