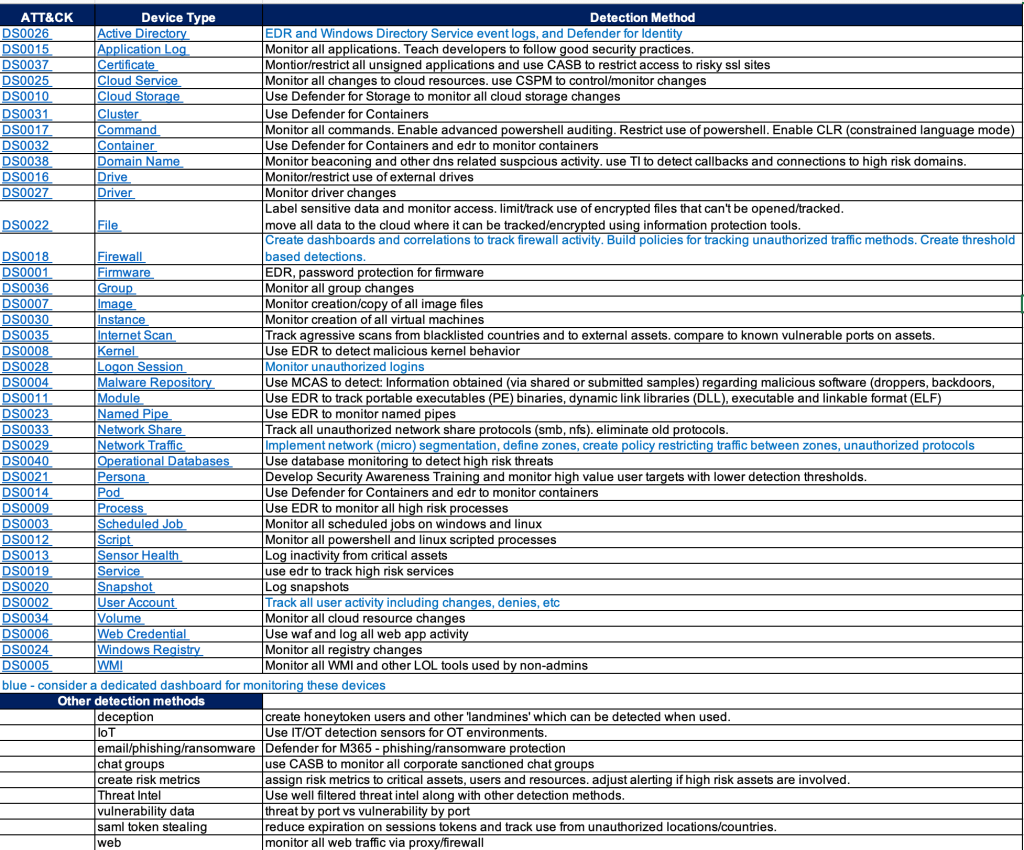
Zero Trust sounds very enticing, but feels overwhelming as much as any other standards based framework.
However there are some quick wins in the Azure world, and all you need is:
- A good checklist (The Microsoft Zero Trust Assessment Quiz)
- A Microsoft Sentinel workbook (see below)
In addition, Microsoft has a ton of direction around Zero Trust like:
If you prefer to save some reading time, I’ve taken Microsoft Zero Trust Assessment Quiz results and compressed it into a clean list of questions here:
Microsoft has also added a Zero Trust workbook to Azure Sentinel, so if you’re using their SIEM, there’s an excellent report that you can export and have a full list of security tool recommendations that you likely already own (depending if you have an E3 or E5 license)
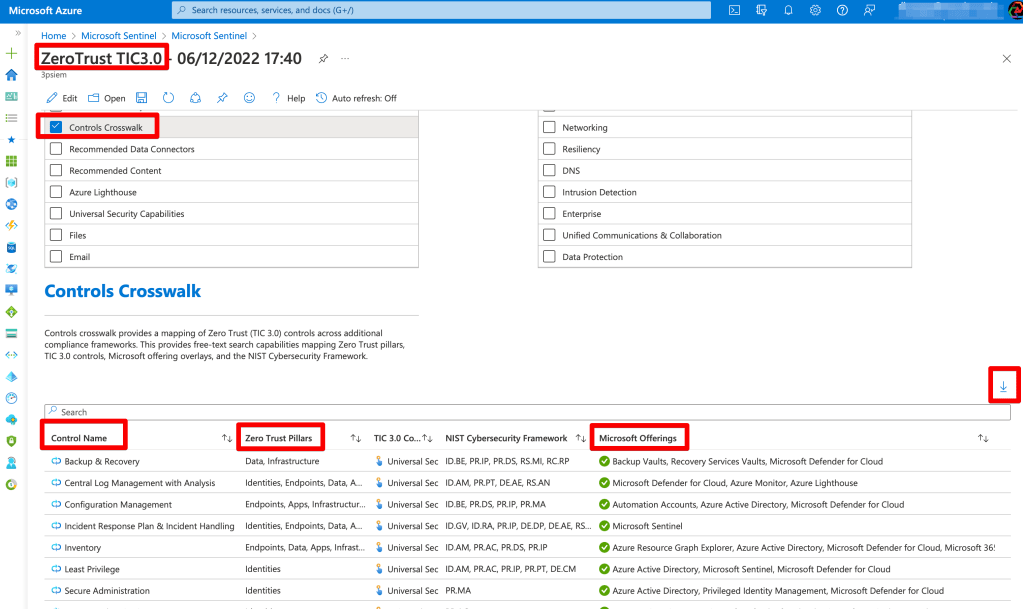
If you’re familiar with the resources under ‘Microsoft Offerings’ then you can begin planning your Zero Trust controls around these features. If you’re not familiar then now it the time to begin learning and proposing a Zero Trust approach around these tools.
Enjoy!