So I skimmed NIST 800-160 V2 – it’s all about ‘Cyber Resiliency’.
What is cyber resiliency?
“The ability to deliver an intended outcome, despite adverse cyber events”
My thoughts on NIST 800-160 vol 2:
Once you understand the basics you might consider these points as a starting approach:
Perform a ‘cyber resilience maturity audit’
Using 800-160 V2 create a checklist to discuss and better understand your organization’s maturity around cyber resiliency.
Identify security tools to enable and improve on your cyber resiliency, eg:
Microsoft Defender for Cloud – Use the built in NIST regulatory standsards to enforce configuration of resources with resilience – eg. don’t allow VMs without backups enabled and redundancy features configured.
O365 Compliance Manager – Create assessments using the NIST templates to identify misconfigurations.
Microsoft Secure Scores – use the several available Secure Scores in O365 and Azure to improve security posture.
Sentinel – Configure alerts to monitor resiliency related issues.
Some more references…
High level objectives:
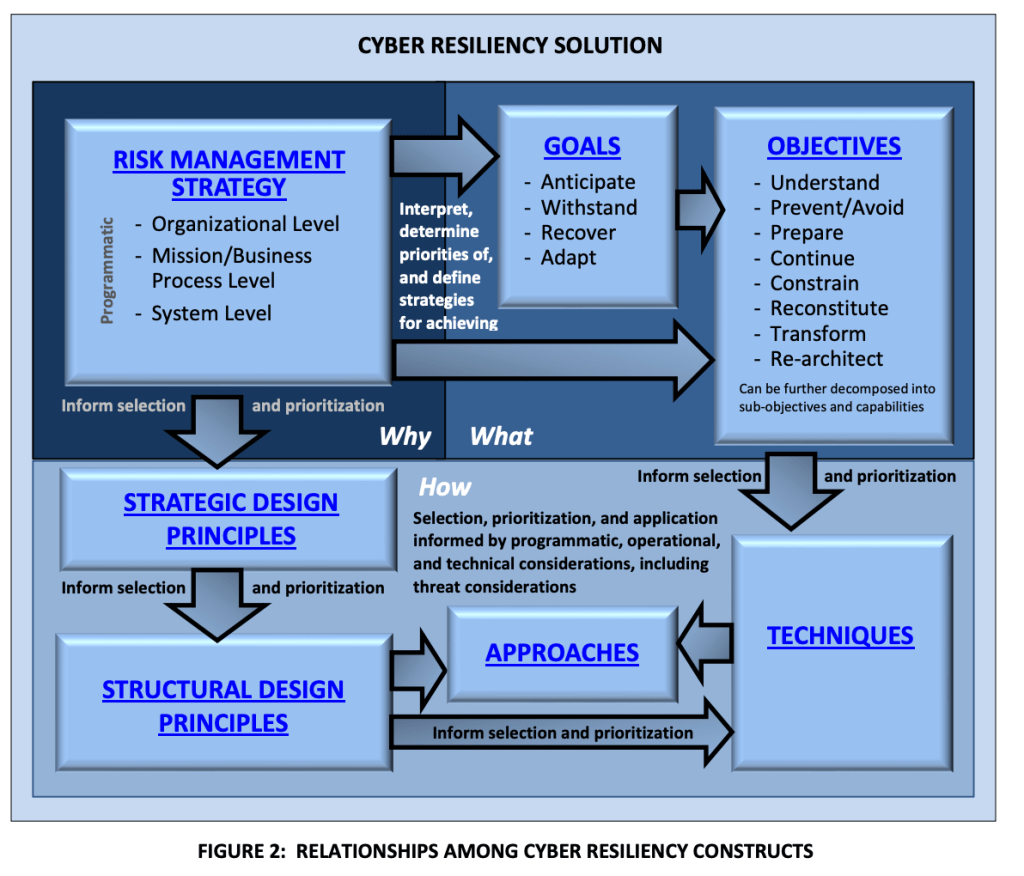
Areas in red can be monitored using Sentinel and Defender for Cloud (and possibly more, just what I know about):
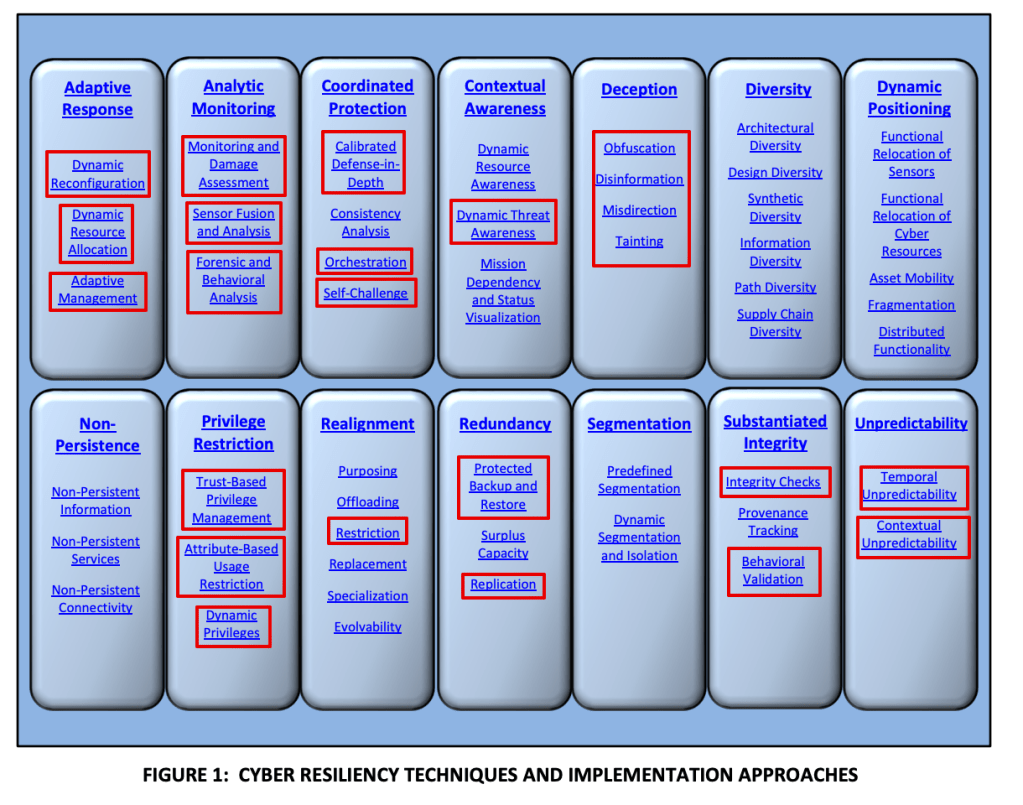
Here is where 800-160 refers to other NIST controls, some of which are templates within Defender for cloud and O365 Compliance Manager (800-70 and 800-37 are premium templates so extra $$):


References
CSF – general cyber security framework
https://www.nist.gov/cyberframework/framework
800-53 – Security and Privacy Controls for Federal Information Systems and Organizations
800-171 – information protection
800-160 – Cyber Resiliency
