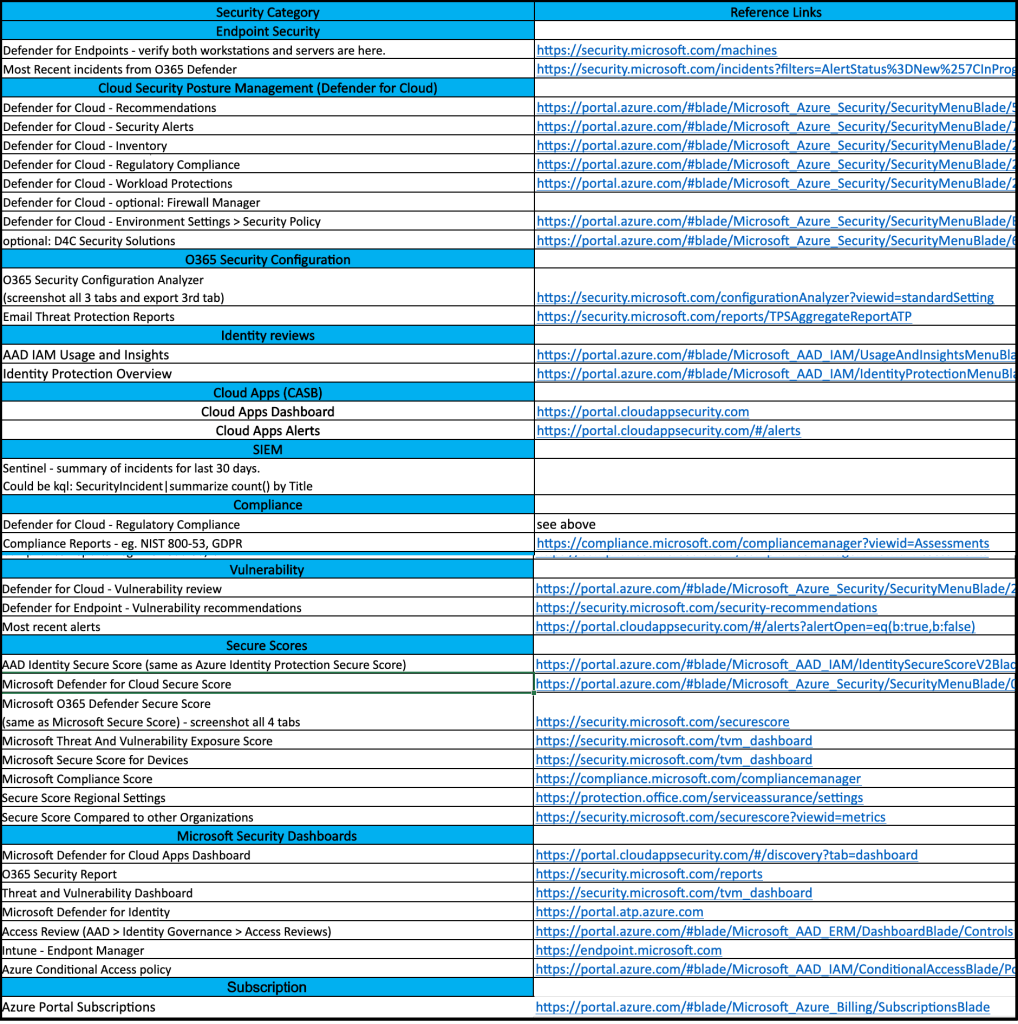
Monitoring an adversary’s movements as it relates to your organization.
Your SIEM likely contains a great deal of information which can be mapped by country. That’s all you need to get started with a dashboard to see at a high level how those countries – or adversaries – are affecting your organization’s security posture.
Start with creating dashboards for the following, using Russia as an example:
- outside > in: top destination IPs/domains FROM Russia
- inside > out: top ip/domain sources TO Russia
- users associated with any Russian IPs/domains.
- asset mapping by criticality associated with Russian IPs (this asset list is likely something you’d have to build, but hopefully you’re already maintaining a good asset list)
- timeline graph – all activity from all sources by volume over time associated with Russian IPs/domains
Some SIEMs are better than others with mapping IPs/domains to a country.
Here’s a query example for doing it in Microsoft Sentinel on WAF events using a geoip reference table:
let geoData =
materialize (externaldata(network:string,geoname_id:string,continent_code:string,continent_name:string,
country_iso_code:string,country_name:string,is_anonymous_proxy:string,is_satellite_provider:string)
[@"https://raw.githubusercontent.com/datasets/geoip2-ipv4/master/data/geoip2-ipv4.csv"] with
(ignoreFirstRecord=true, format="csv"));
let lookup = toscalar( geoData | summarize list_CIDR=make_set(network) );
AzureDiagnostics
| where Category contains "ApplicationGateway"
| where Message contains "Inbound Anomaly Score Exceeded"
|summarize by clientIp_s
| mv-apply list_CIDR=lookup to typeof(string) on
(
where ipv4_is_match (clientIp_s, list_CIDR) //== false
)
| join kind=rightouter (AzureDiagnostics | where TimeGenerated > ago(7d)) on clientIp_s
| join kind=leftouter
(
geoData
) on $left.list_CIDR == $right.network
|summarize count() by clientIp_s, country_name, hostname_s
|where clientIp_s <> ""
|order by count_ desc
| where country_name == "Russia"
| where count_ >= 10Next, research past history from attackers in that country. Go to Mitre’s ATT&CK site and search for the attack groups of interest:
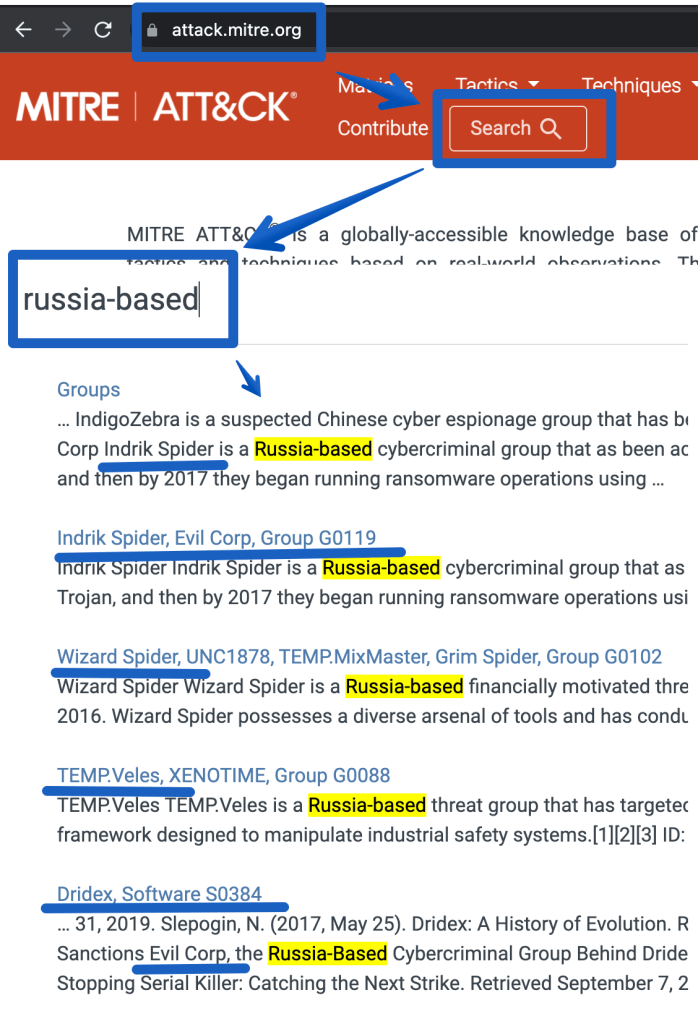
That provides the following references.
https://attack.mitre.org/groups/G0007 (APT28)
https://attack.mitre.org/groups/G0074 (Dragonfly 2.0)
https://attack.mitre.org/groups/G0016 (APT29)
https://attack.mitre.org/groups/G0119 (Indrik Spider, Evil Corp)
https://attack.mitre.org/groups/G0133 (Nomadic Octopus)
https://attack.mitre.org/groups/G0034 (Sandworm)
https://attack.mitre.org/groups/G0088 (Temp.veles)
https://attack.mitre.org/groups/G0010 (Turla)
https://attack.mitre.org/groups/G0053 (FIN5)
https://attack.mitre.org/groups/G0102 (Wizard Spider)
The next step would be to go deeper and identify ‘entities’ that are specific to using these attacks, such as:
- IP/domains from threat intel feeds
- attacks/techniques that map to the above attack groups in the ATT&CK matrix. Click on the links above to see more details.
(eg. T1059 – powershell scripting using Empire) - malware/endpoint (EDR) and network detections (proxy/nids/firewall) specific to the ATT&CK groups listed above. Many of these tools support ATT&CK mappings so with some luck you just have to create a list of the Mitre Technique numbers (eg. T1059) and you’re off.
- Use the information above to create SIEM correlations. Add these alerts to your workbook/dashboard to show near real time detections as they are seen. Example correlations may include:
- events mapping to a threat intel feed related to the adversaries in question
- alerts related to 4 or more distinct Mitre Techniques in question.
- EDR/IDS events mapping to the adversaries in question
- malware NOT cleaned AND traffic to Russia or a known-bad-ip for the past 15 minutes.
- SOAR example: create a playbook to map all alerts to APTs and TAG them as ‘MITRE APT: Russia’ use threat intel for the logic or another detection method)
- Add metrics to your dashboard for management to see MTTD/MTTR (mean time to detect/respond).
Peace to all.
More Ukraine related information intelligence:
https://github.com/Orange-Cyberdefense/russia-ukraine_IOCs
https://github.com/curated-intel/Ukraine-Cyber-Operations
https://www.mandiant.com/resources/apt-groups
https://www.mandiant.com/resources/insights/ukraine-crisis-resource-center
Some more KQL queries to try:
Alerts by IP:
-----------
let IP_Data = external_data(network:string,geoname_id:long,continent_code:string,continent_name:string ,country_iso_code:string, country_name:string,is_anonymous_proxy:bool,is_satellite_provider:bool)
['https://raw.githubusercontent.com/datasets/geoip2-ipv4/master/data/geoip2-ipv4.csv']
with (ignoreFirstRecord=true, format="csv");
SecurityAlert
| where TimeGenerated > ago(120h)
| extend AlertEntities = parse_json(Entities)
| mv-expand AlertEntities
| extend IPAddress = tostring(AlertEntities.Address)
| summarize count() by IPAddress
| where isnotempty(IPAddress)
| evaluate ipv4_lookup(IP_Data, IPAddress, network)
//| where country_name != "United States"
| where country_name == "Russia"
|project IPAddress, count_
|order by count_ desc
|render columnchart
------------
Alerts timeline:
let IP_Data = external_data(network:string,geoname_id:long,continent_code:string,continent_name:string ,country_iso_code:string, country_name:string,is_anonymous_proxy:bool,is_satellite_provider:bool)
['https://raw.githubusercontent.com/datasets/geoip2-ipv4/master/data/geoip2-ipv4.csv']
with (ignoreFirstRecord=true, format="csv");
SecurityAlert
| where TimeGenerated > ago(120h)
| extend AlertEntities = parse_json(Entities)
| mv-expand AlertEntities
| extend IPAddress = tostring(AlertEntities.Address)
| summarize count() by IPAddress, DisplayName, ProviderName, bin(TimeGenerated, 1h)
| where isnotempty(IPAddress)
| evaluate ipv4_lookup(IP_Data, IPAddress, network)
| where country_name != "United States"
//|project TimeGenerated, country_name, IPAddress, ProviderName, DisplayName
| where country_name == "Russia"
//|project IPAddress, DisplayName,ProviderName, count_
//|order by count_ desc
|render timechart
--------------
Malicious traffic: Malicious domain and port (syslog data)
CommonSecurityLog
| extend Country=MaliciousIPCountry
|where TimeGenerated >ago(7d)
|where Country == "Russia"
|where DestinationIP == ""
//|extend HostPort = strcat(DestinationHostName, "-port-", DestinationPort)
|summarize count() by DestinationHostName, DestinationPort
|order by count_ desc
-------------
Top Malicious IPs (syslog data)
CommonSecurityLog
| extend Country=MaliciousIPCountry
|where TimeGenerated >ago(7d)
|where Country == "Russia"
|where DestinationIP == ""
|summarize count() by MaliciousIP
|order by count_ desc
|limit 10
-------------
Destination IPs by Count (CommonSecurityLog)
let IP_Data = external_data(network:string,geoname_id:long,continent_code:string,continent_name:string ,country_iso_code:string, country_name:string,is_anonymous_proxy:bool,is_satellite_provider:bool)
['https://raw.githubusercontent.com/datasets/geoip2-ipv4/master/data/geoip2-ipv4.csv']
with (ignoreFirstRecord=true, format="csv");
CommonSecurityLog
| where TimeGenerated > ago(1h)
| where DestinationIP !startswith "192."
| where DestinationIP !startswith "10."
| where DestinationIP !startswith "127."
| where DestinationIP !startswith "171."
| summarize count() by SourceIP, DestinationIP, DestinationPort, SimplifiedDeviceAction, DeviceVendor, bin(TimeGenerated, 1h)
| where isnotempty(SourceIP)
| evaluate ipv4_lookup(IP_Data, SourceIP, network)
| where country_name != "United States"
//|project TimeGenerated, country_name, IPAddress, ProviderName, DisplayName
| where country_name == "Russia"
|summarize count() by SourceIP
|render columnchart
-----------
Palo Alto - Threat events by country
let IP_Data =
external_data(network:string,geoname_id:long,continent_code:string,continent_name:string ,country_iso_code:string, country_name:string,is_anonymous_proxy:bool,is_satellite_provider:bool)
['https://raw.githubusercontent.com/datasets/geoip2-ipv4/master/data/geoip2-ipv4.csv']
with (ignoreFirstRecord=true, format="csv");
CommonSecurityLog
| where TimeGenerated > ago(1d)
| where DestinationIP !startswith "192."
| where DestinationIP !startswith "10."
| where DestinationIP !startswith "127."
| where DestinationIP !startswith "171."
| where DeviceVendor == "Palo Alto Networks"
| where Activity == "THREAT"
//| summarize count() by SourceIP, DestinationIP, DestinationPort, ApplicationProtocol, Activity, SimplifiedDeviceAction, DeviceVendor, Message, RequestURL,FlexString2,bin(TimeGenerated, 1h)
//| where isnotempty(SourceIP)
| evaluate ipv4_lookup(IP_Data, DestinationIP, network)
| where country_name != "United States"
//|project TimeGenerated, country_name, IPAddress, ProviderName, DisplayName
|summarize count() by country_name
|order by count_ desc
|render columnchart
-----------------